AWS - IAM
- Identity Access Management
- AWS 리소스 접근 제어
AWS Identity
- Root Account
- Administrator
- AWS web console & AWS API
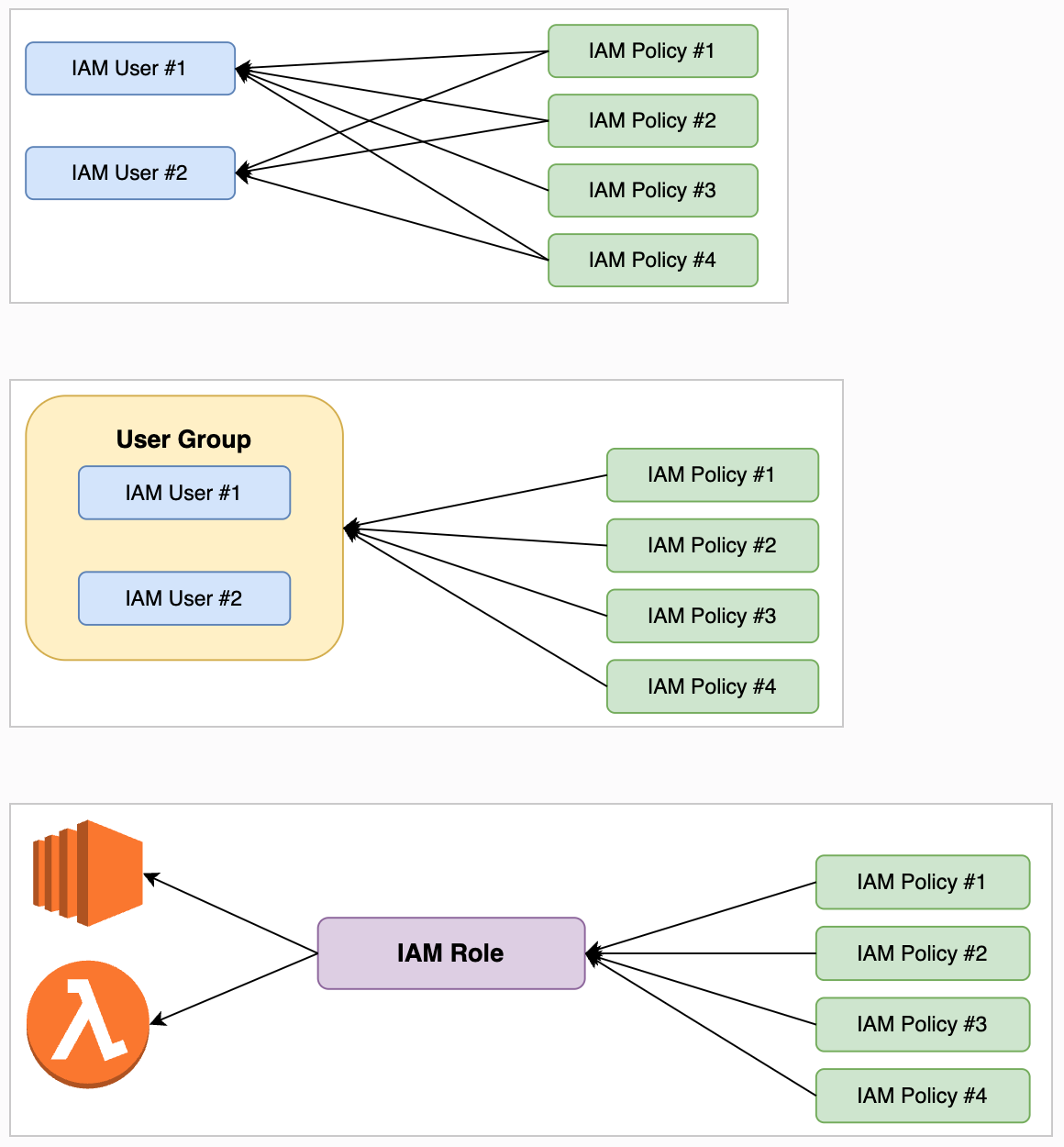
- IAM - User, Role
- 제한된 AWS Web console & AWS API
- STS (Security Token Service)
- 제한된 AWS web console & AWS API
- life-time
AWS IAM Policy
- AWS 서비스와 리소스에 대한 인가 기능 제공
AWS IAM Policy 종류
- SCP (Service Control Policy)
- AWS Organizations 내 정책
- OU or AWS Account 레벨에서의 정책
- Permission Policy, Permission Boundary
- IAM User, Role에 대한 정책
- Boundary: IAM User, Role에 할당된 권한 제한
- Session Policy
- STS, Federation시 권한 제어
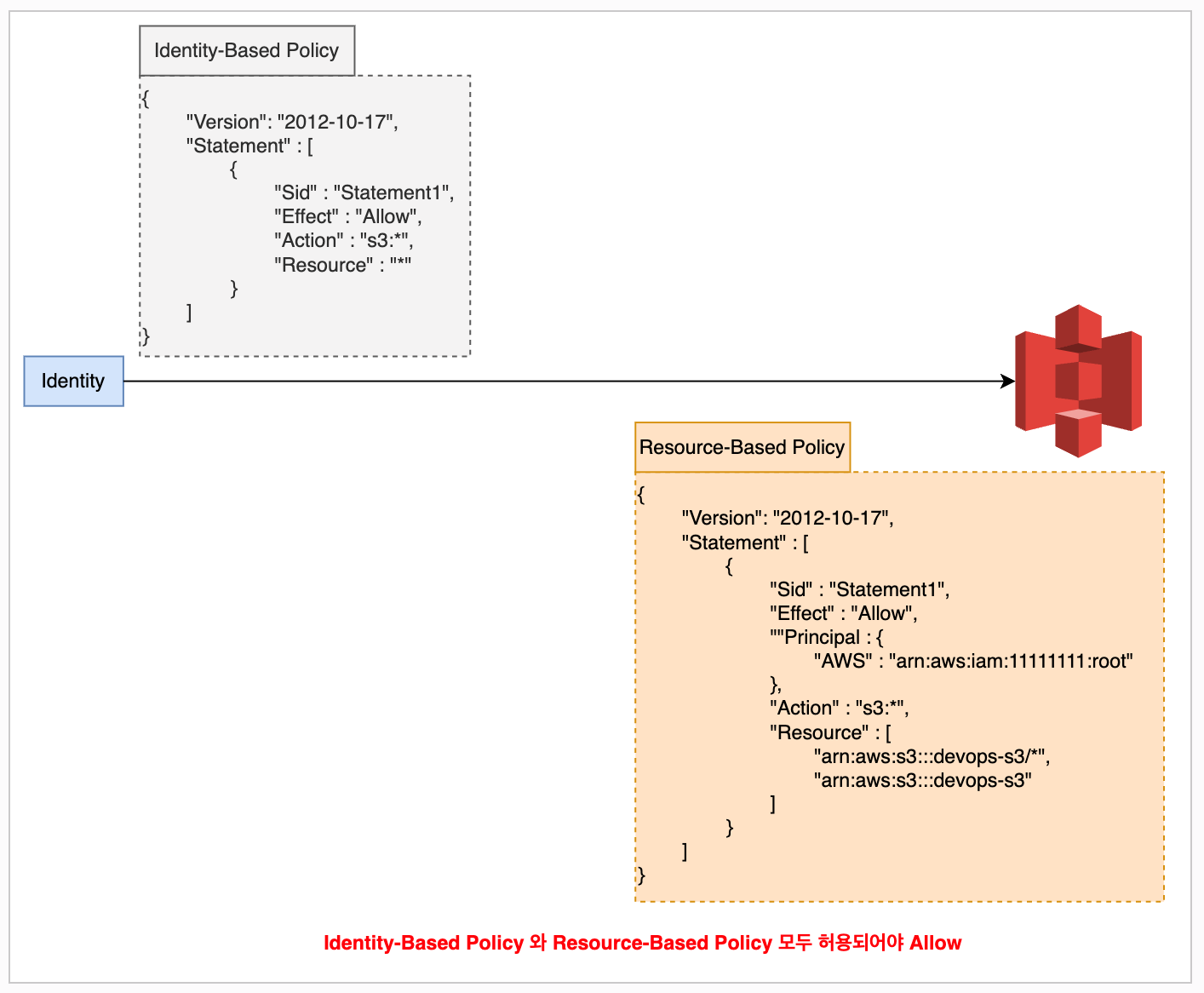
- Resource-based Policy
- Identity가 아니라 AWS Resource자체에 권한 제어
- S3, SQS, KMS, ECR, ...
- Endpoint Policy
- Gateway type vpc endpoint
AWS IAM Policy (JSON Format)
{
"Statement" : {
"Effect": "Allow",
"Principle": {
...
},
"Action": [
"ec2:*"
],
"Resource": [
"*"
],
"Condition": {
...
}
}
}
IAM Policy Example #1
{
"Version" : "2012-10-17"
"Statement" : [
{
"Sid": "DenyAllButProductManagers",
"Effect": "Deny".
"Principal" : {
"AWS" : "*"
},
"Action" : [
"s3:PutObject"
],
"Condition" : {
"StringNotEquals" : {
"aws:PrincipalTag/job-title": "Product-Manager"
}
}
}
]
}
AWS IAM Use Case
AWS Access Management
- Resource를 생성하지 않은 다른계정
- Organation SCP and Identity-Based-Policy and Permissions-Boundary and Resource-Based-Policy
- Resource를 생성한 동일계정
- Organation SCP or Identity-Based-Policy or Permissions-Boundary or Resource-Based-Policy